In brief:
- Business identity theft is when criminals pose as a business or its representatives – by stealing the ID information of a business or its staff, copying the business’s branding designs, or both – to commit fraud by fooling customers and other businesses into giving up money or sensitive information.
- You can guard against business identity theft by regularly checking your records and credit score, making sure your Secretary of State and intellectual property registrations are up to date, establishing policies and training regimens regarding cybersecurity and data privacy & protection, and investing in identity theft insurance.
- To avoid onboarding a fake business, check its ID information against multiple credible sources, look for information that may point to it being high-risk, verify the identities and risk profiles of its ultimate beneficial owners (UBOs), conduct enhanced due diligence if necessary, and continue to monitor the business’s information and activities even after onboarding it.
Incidents of criminals posing as businesses to steal money and sensitive information are more common – and costly – than you might think. As summarized by Market.us Scoop, several U.S. government and professional sources have reported on business identity theft statistics over the past several years. One stat that stands out is that nearly half of all businesses worldwide had to handle at least one identity theft incident in 2022. And the average cost of each of those incidents was $140,000.
Small business identity theft is on the rise, too. According to a report by Regula Forensics and Sapio Research, although small and medium-sized businesses typically have to deal with fewer identity theft incidents than enterprises, they are targeted almost as often. 90% of SMBs worldwide experienced identity theft attempts in 2022 – only a slightly lower rate than the 95% of large companies that faced at least one identity theft attack that year.
So what is business identity theft, and how does it happen? What can your company do to protect itself from identity thieves? What steps should it take to avoid onboarding a fake company? And what tools can it use to make detecting and preventing identity theft easier? This article has the answers.
- What is business identity theft?
- 9 examples of business identity theft scams and tactics
- 8 strategies for how to prevent business identity theft
- Business verification measures for detecting fake companies
- 6 best identity theft business solutions to avoid onboarding fake companies
Our first step is defining what business identity theft is, and what kind of identity information criminals are looking for to help them carry it out.
Business identity theft is when criminals pose as a business or people associated with it (sometimes even stealing their ID information). By doing so, they can commit fraud such as stealing cash, abusing lines of credit, illegally applying for business loans, or filing fake business tax returns.
Identity theft’s impact on a business extends beyond just lost revenue. Many businesses have to slow or stop their operations to restore stolen, destroyed, or altered documents, re-register the business with the appropriate regulators, and fight legal battles to retain ownership of their intellectual property. They also tend to lose the trust and patronage of several existing and potential customers.
What information are business identity thieves after?
Business identity thieves want information that allows them to trick customers, partner businesses, financial institutions, government agencies, and others into thinking they’re legitimate business representatives. That’s how they pull off their scams.
They’re also looking for credentials that allow them to break into a business’s accounts and sensitive data files. They want to steal money, but they’re also looking for information they can use to target their next victims.
Examples include:
- Owner, officer, or employee personal information: This allows criminals to create the impression that they’re someone legitimately associated with a business when they really aren’t.
- Office addresses: If identity thieves know where a business is located, there are a number of ways they may be able to find its other identity information by going there. Or they may set up a fake office or storefront nearby that mimics the real business, aiming to trick customers and others into giving away money and sensitive information.
- Employment Identification Number (EIN): This can allow criminals to get unwarranted business tax benefits from the IRS via business identity theft by filing false tax returns.
- Other business registration numbers: Acquiring a business’s Company Registration Number (CRN), state registration number, industry license/permit number, or Registered Identification Number (RN) can help criminals further the ruse that they represent a legitimate business
- Financial and payment account credentials: These can allow identity thieves to steal money directly from a business, run up large debts on the business’s lines of credit, or take out loans that they never intend to repay in the business’s name.
- IT system account credentials: These allow criminals to break into a business’s IT systems and potentially steal all manner of information.
- Customer or supplier lists: Using these in combination with the business’s other ID information, identity thieves can extend the fraud beyond just the business itself. They can contact the business’s customers or partners while pretending to be the business and ask for money or sensitive information, or initiate bogus transactions that only benefit themselves.
- Trade secrets: Identity thieves may also target registration information regarding a business’s intellectual property. They use it along with the business’s other stolen credentials to file a trademark, copyright, or patent while claiming to be the business. Then they extort money from the real business in exchange for it getting its stolen intellectual property back.
Protecting this information is why it’s so important to “Know Your Business” (KYB) at every stage of your company’s growth. You need to know exactly who you’re doing business with, whether they are who they claim to be, and how much their activities and history point to a chance that they’ll harm your company (either directly or indirectly).
To help you out, we cover how our Verify product can help you scale your company while still keeping it safe and fulfilling its compliance obligations. Have a look at our demo below.
{{gated-content-block="/events/productdemo-verify-june-2025"}}
So how does identity theft for business happen? Well, criminals have come up with all sorts of tricks to get the business ID information they need to scam their targets. And sometimes they don’t even need this information – they just need to look convincingly enough like the real business to trick people into giving them access to financial (and other) accounts.
Here are some examples of business identity theft tactics so you can see what kinds of things criminals might try to fool you, your customers, and your partner businesses out of their money and sensitive information.
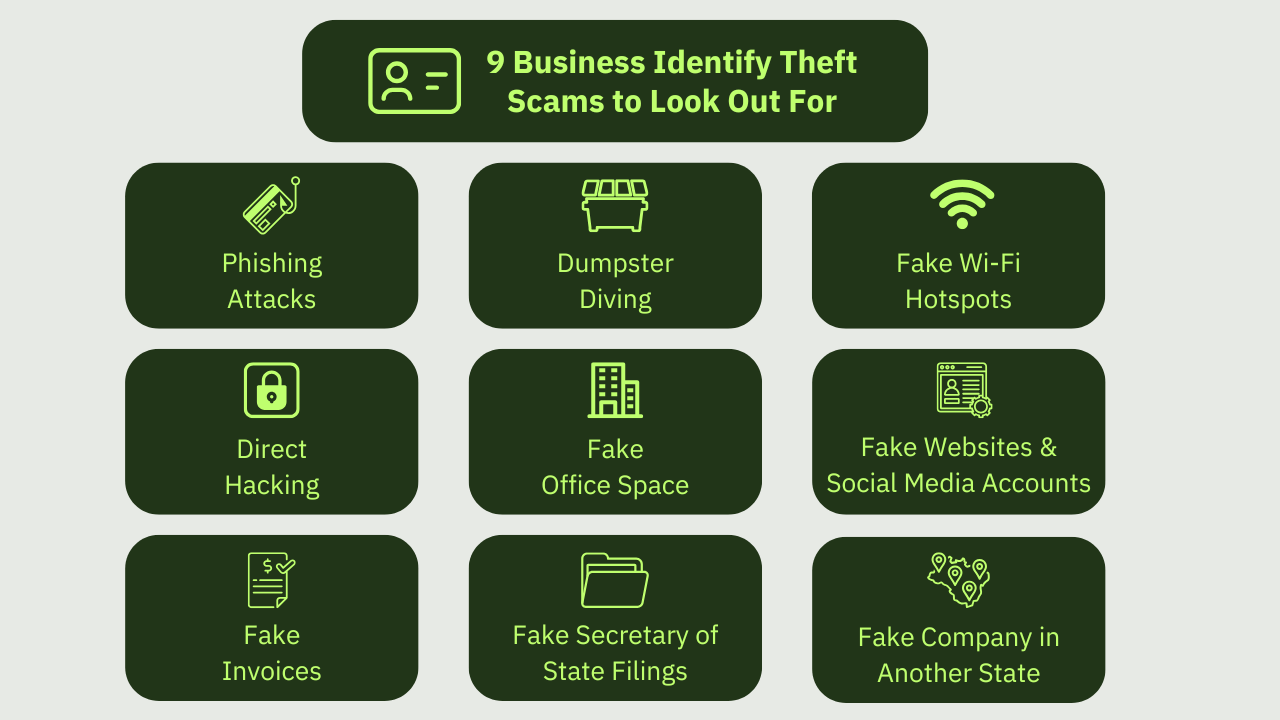
1. Phishing attacks
Phishing is a common fraud tactic in which criminals send a message to someone at a business that mimics the style and tone of another business or institution they trust. Often, they will steal logos or other graphics from the real organization to make the message look authentic.
The message directs the person to respond with sensitive business information, such as IT access credentials or bank account login credentials. Either that, or it tells them to click through to a fake website that either deceitfully collects the sensitive information or downloads malware to steal it.
2. Dumpster diving
Identity thieves will root through a business’s garbage, or even public trash containers, looking for sensitive business documents that weren’t properly destroyed. Those documents may contain identity information about the business or its employees, credentials for IT or financial accounts, and so on.
The thieves can then use this information to convincingly pose as the business or its representatives, if not just directly break into the business’s accounts to steal money and more confidential information.
3. Fake Wi-Fi hotspot
Identity thieves set up an unsecured Wi-Fi hotspot inside or near a business’s office, often mimicking the name of one of the business’s official networks. Their goal is to get an employee to connect to the fake network by mistake, which then allows them to view potentially sensitive information the employee sends over the network (such as account login credentials).
4. Direct hacking
Tech-savvy criminals may be able to find security blind spots in IT software, or even brute-force guess weak passwords, to directly hack into a business’s systems. Once inside, they can steal pretty much any information they want: business & employee ID information, financial account credentials, customer & supplier lists, intellectual property documentation, etc.
5. Fake office space
If identity thieves know where a business’s offices are located, they may rent office space nearby – ideally in the same building – and mimic the legitimate business. Their goal is to trick customers, suppliers, and even financial institutions into giving them money and sensitive information that was meant for the real business.
6. Fake websites and social media accounts
Another tactic criminals use to scam a business’s customers and suppliers without necessarily needing the business’s ID information is setting up fake websites or social media accounts that mimic those of the real business (or its owners, officers, or employees). These can be used to trick people into going to other websites that steal their sensitive information, or to collect payments for products the criminals don’t actually have.
7. Fake invoices
Criminals can also create fake invoices that look like they’re from a business by copying its branding and document layout. They will also include instructions and ID details so victims will send money to them instead of the legitimate company. They can then send those invoices to the business’s clients to trick them into paying money they don’t actually owe.
8. Fake Secretary of State filings
Some very creative identity thieves can use a business’s branding and document layout to forge false requests to a Secretary of State office to change a business’s information on file. For example, they can replace the names of owners or high-ranking officers with their own (fake) names to give themselves executive power over the business. They can then sell the business or its assets to unsuspecting buyers, or commit other kinds of fraud.
9. Fake company in another state
Another scheme identity thieves may pull is creating a business with a very similar name to another business, but registering it in a state where the real business isn’t registered or doesn’t operate. Then the criminals claim they’re the official version of the business, and start rerouting payments and mail meant for the legitimate business to themselves. This not only costs the real business money, but can also expose sensitive information.
A cornerstone of business identity theft protection is taking the right precautions to secure the identities of your business and its associated people. If you want to know how to prevent identity theft in a business, these are some good starting points.
1. Review your records
Periodically compare your bills and account statements to make sure everything adds up. If you notice anything strange on a bill, immediately contact the business that sent it and ask them to justify it. If they can’t, then something is really wrong.
2. Keep an eye on your credit score
Identity thieves like to target businesses with good credit ratings, since that makes it easier for them to trick financial institutions into loaning them large amounts of money that they’ll never pay back. Monitor your business’s credit report – if it takes an unexpected dip, you should take another look at who you’re doing business with.
3. Stay up-to-date with your Secretary of State registration
One way criminals can steal your company’s identity is by contacting the Secretary of State office in a state where you operate and asking to change the information. To guard against this, make sure the information each relevant Secretary of State office has on your company is current.
Some Secretary of State offices offer additional information security features, such as two-factor authentication (2FA) for accessing your business file and automated email alerts if any information on your file changes. Sign up for these to further secure your business information and to know if someone has made an unauthorized change to it.
4. Get automated alerts from your financial institutions and other creditors
If possible, you should also sign up for automatic alerts from banks, lenders, and other businesses that provide services for your company. That way, if something changes unexpectedly – like someone opening a new account or taking out an additional loan – you can inquire about it quickly and get it sorted out before fraudsters do any significant damage.
{{related-content-block="/blog/ongoing-compliance"}}
5. Establish policies for protecting your company’s sensitive information
You should have a system in place for how to handle and secure identity information about your company, its staff, its customers, and its partner businesses. It should contain things like:
- Making staff aware of what kinds of information need to stay confidential
- Keeping important paper business documents locked in cabinets and secure rooms
- Keeping important digital business documents protected by strong passwords
- Reserving access to important business documents for staff who really need it
- Properly destroying business documents and data devices before disposing of them
6. Train staff on cybersecurity and data protection best practices
It can only take one of your staff members falling for an identity thief’s tricks or otherwise being careless to put your company’s ID information at risk. This is especially true in the digital world, where actions happen and information moves almost instantaneously.
Make your staff aware of how they can safeguard both company and private information whether they’re online or offline. Examples include:
- Knowing how to recognize and deal with phishing attacks and suspicious emails
- Having different accounts for their company and personal emails
- Securing their company accounts with strong passwords and 2FA (if available)
- Not sharing sensitive information over email or any public web service
- Using anti-malware software and network firewalls on their devices
- Backing up sensitive information to a secure place outside your company’s network
- Only entering personal information on secured websites (https://)
7. Officially register your company’s intellectual property
Avoid having your company’s name, logo, patents, or other intellectual property held for ransom. Trademark these things first to block identity thieves from stealing them and then trying to claim ownership.
8. Invest in business identity theft insurance
Some business insurance packages will cover losses and costs if your company’s identity is stolen and used for fraud. These can include credit monitoring fees, legal fees, restoration costs, and sometimes even lost income. Do some research into what each insurance plan costs and covers (or doesn’t cover) to see if it would be worth it for your company.
In the previous section, we shared advice on how to prevent business identity theft for your own company. But how do you go about identity theft protection for your business from fraudsters who have stolen another business’s identity or just made one up for themselves?
Onboarding a business with a stolen or fake identity can cause numerous problems. Criminals can steal large sums of money from you, or even steal the identity information of your customers, suppliers, and partners to commit further fraud.
To detect identity theft of a business, here’s what you need to do.
1. Find the business’s ID information and check it against official sources
To stay compliant with FinCEN’s CDD Final Rule, your KYB process has to collect and verify a business’s:
- Legal name
- Operating addresses
- Taxpayer Identification Number (usually an EIN)
- Business registration status
- License or permit documentation (if applicable)
2. Search for and assess risk-indicating information about the business
Even if a business’s ID seems to check out, there can be other signs that it’s not legitimate. Check sources like national and international sanctions lists and financial watchlists, credit bureaus, lien filings, bankruptcy and other legal proceedings, industry classification codes, and even the news to look for clues.
For example, you might find the business is operating in an industry, region, or both that are known to be risky. Or you may find it actually has bad credit from lawsuits, bankruptcies, and UCC or tax liens; having a thin credit history can be suspicious as well. It may even be in the news as part of an investigation into business identity theft cases.
3. Identify and perform KYC on the business’s UBOs
Next, you need to find out who’s ultimately controlling and benefiting from the business: the ultimate beneficial owners (UBOs). You should be able to get this information from the same government sources you got the business’s other identifying information from. At minimum, you should get each person’s name, home address, date of birth, and an ID number from an official government identification document (such as a passport).
But another part of “Know Your Customer” (KYC) is looking deeper into each UBO’s history for risk signals, such as asking yourself these kinds of questions:
- How wealthy are they?
- Do they live in a country on a sanctions list or financial watchlist, or are they on one of these lists themselves?
- Are they a politically exposed person (PEP)?
- What does their financial history look like from other financial institutions they’ve been a customer of?
- Why is the customer opening an account and what do they intend to use it for?
- Have you conducted any kind of risk assessment on them based on the information you’ve collected here?
Answering these kinds of questions should allow you to spot people behind businesses who may be risky to deal with, or could even be outright fakers.
4. Perform EDD if you still have doubts
If your initial investigations find too much missing or inconsistent information – or too many risk signals – regarding a business, you can take things a step further by performing enhanced due diligence (EDD). To do so, find answers to questions such as:
- What are the UBOs’ sources of income?
- Does a UBO’s income line up with how much property they have?
- What is the business’s organizational structure (partnership, LLC, corporation, etc.)?
- How is the business funded, and who runs its daily operations?
- How does the business relate to its parent company, subsidiaries, suppliers, and clients?
- Can I confirm the business physically exists by visiting its offices?
- Do they have any adverse media presence or does the news suspect them of being involved in criminal activities?
- Can anyone at the company provide any information or documents I’m missing?
This should allow you to make a final decision on whether a business is too risky to onboard, or might even be an imitation that stole the identity of a legitimate business.
{{related-content-block="/blog/cip-cdd-edd"}}
5. Continue to monitor the business’s activities and relationships
If you eventually decide to onboard the business, you aren’t entirely safe yet. Watch the business closely for unusual activities – especially transactions that form odd patterns or are made for strange purposes, or even changes in the business’s ownership or management structure. All of these could point to the business not being what it claims to be.
Software tools for business identity theft prevention typically fall into one of two categories. The first is software that proactively works to protect you from business identity theft through means such as cybersecurity monitoring and business verification & risk assessment. The second is software that reactively finds evidence of business identity theft and helps you mitigate and recover from the damage. Here are some of the top identity theft business solutions of both kinds.
1. Middesk
Middesk can use its direct connections to Secretary of State offices and other U.S. government agencies to look up and verify information on any U.S. business identities – all 100+ million of them — as well as alternative and contextual data, which can provide a much more comprehensive picture and uncover additional risk signals.
Middesk also has numerous risk assessment features that can give you deeper insight into whether a business is above board or not, even if its ID details check out. These include sanctions list and financial watchlist screening, adverse media screening, and KYC checks of a business’s UBOs – even PEP and RCA screening.
How pricing works: Contact Middesk for a custom pricing model based for your business.
Best for: Total coverage of U.S. businesses for verification, and strong risk assessment capabilities.
2. NordStellar
Created by the makers of NordVPN, NordStellar is a comprehensive identity theft prevention suite tailored to businesses. A solution that can scale to protect your business and its employees from identity theft, NordStellar offers proactive identity theft features such as data breach monitoring, dark web monitoring, external vulnerability scanning, cybersquatting detection, and more.
It doesn't come with identity theft insurance, though, and it focuses mostly on preventing cyberattacks – meaning it can’t defend you as well (or at all) from other methods of identity theft.
How pricing works: Contact them for a demo and a custom quote.
Best for: One of the few top identity theft solutions designed specifically for businesses.
Get a personalized demo for NordStellar.
3. LifeLock by Norton
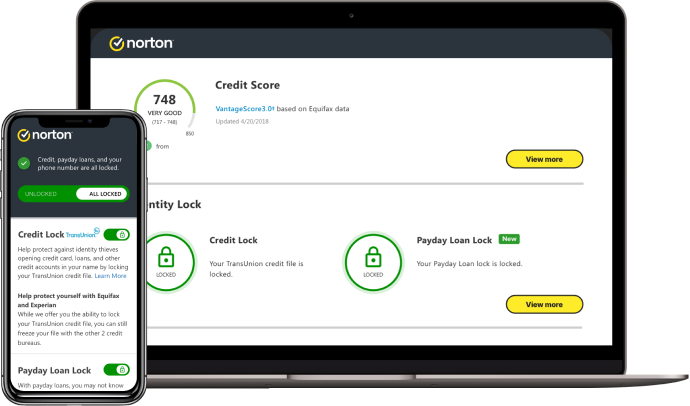
LifeLock by Norton provides dark web monitoring, data breach notifications, and solid credit monitoring capabilities. It also provides up to $3 million in identity theft insurance – that can include stolen funds, personal expenses, and fees for lawyers & other experts – to help restore your business’s identity and other assets if they get stolen.
While LifeLock’s introductory prices are affordable, they increase significantly after the first year. LifeLock also has no cybersecurity abilities and can’t actually stop identity theft; the best it can do is watch for signs, minimize the damage, and help you recover. That’s why it’s recommended to pair LifeLock with a Norton 360 cybersecurity solution for small businesses.
How pricing works: Tiered subscription service starting at $5/month, up to $35/month.
Best for: Monitoring both personal and business credit by checking them at any time.
Visit lifelock.norton.com and see which plan is right for you.
4. Aura
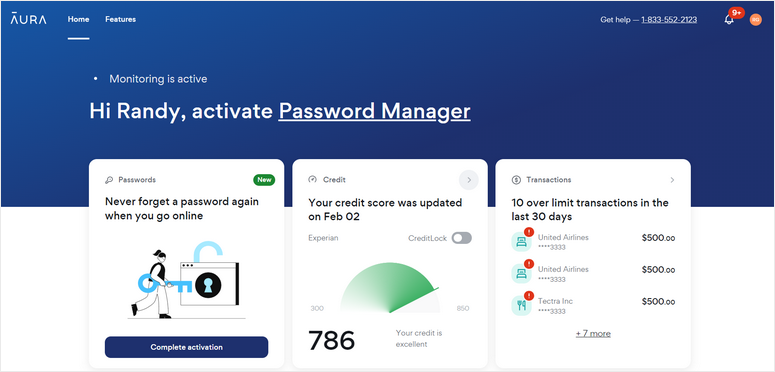
Aura’s identity theft protection solution comes with plenty of features, including account breach monitoring, personal information monitoring, home & auto title monitoring, 3-bureau credit monitoring, an Experian credit lock, and up to $1 million identity theft insurance for each adult user (up to $5 million). It also includes some cybersecurity functions such as anti-malware, virtual private networks (VPNs), and a password manager. And you get all of this in an easy-to-use interface for a very affordable price.
Some of Aura’s downsides are that it has limited social media account and dark web monitoring capabilities, only gives you credit reports once a year, and can’t lock your credit file with Equifax or TransUnion. In addition, its cybersecurity features don’t scale well in a business setting.
Aura offers a small business program where you can buy licenses in bulk at a discount, but you have to contact the company to inquire about it.
How pricing works: Tiered subscription service starting at $12/month, up to $50/month.
Best for: Powerful identity theft monitoring that’s easy to use and great value for money.
Learn more about Aura for small businesses.
5. Ondato

Ondato’s strength is its powerful and flexible options for verifying the identities of businesses and their owners: photo-based, video-based, document upload-based, and now near-field communication-based. Ondato recognizes over 10,000 types of identity documents from 195 different countries, and can identify UBOs in 50 of those countries.
You can choose multiple identity verification options, but this can make Ondato more expensive and complicated to set up. At any rate, Ondato’s specialty is in verifying the identities of individual people as opposed to businesses. So its risk detection and assessment capabilities, especially for businesses, also seem somewhat limited.
How pricing works: Contact for a free demo and a quote.
Best for: Multiple identity verification options for both KYB and KYC.
Have a deeper look into what Ondato’s business verification services can do.
6. iDenfy

iDenfy offers customizable business verification services that give you greater control over your KYB workflow. It connects to over 180 company registries from over 120 countries, contains several automation options, and allows for creating custom questionnaires to screen businesses.
The downside is that you have to configure most of these settings yourself, and enabling too many can slow down your business onboarding by adding too much friction to the verification process.
How pricing works: Custom quote based on services needed and monthly transaction volume.
Best for: A modular KYB platform that can be adapted to specific threats and business niches.
Get more information on how iDenfy’s KYB solution works.
Middesk’s business verification and risk assessment tools help protect your company from associating with criminals who are using a stolen business identity. It automates checks for business ID information at Secretary of State offices and other U.S. government agencies like the IRS and SEC, so you can confirm whether a business’s information is consistent across multiple sources.
It can also automate client onboarding by gathering information on the potential risk level of the entity such as presence on financial sanctions or watchlists, adverse media coverage, involvement in lawsuits, risky industry classifications, and more.
Contact us for a demo to see everything Middesk can do to keep identity thieves posing as businesses out of your commercial customer and partner networks.